REPORT SUSPICIOUS ACTIVITY
SUBMIT A TIP
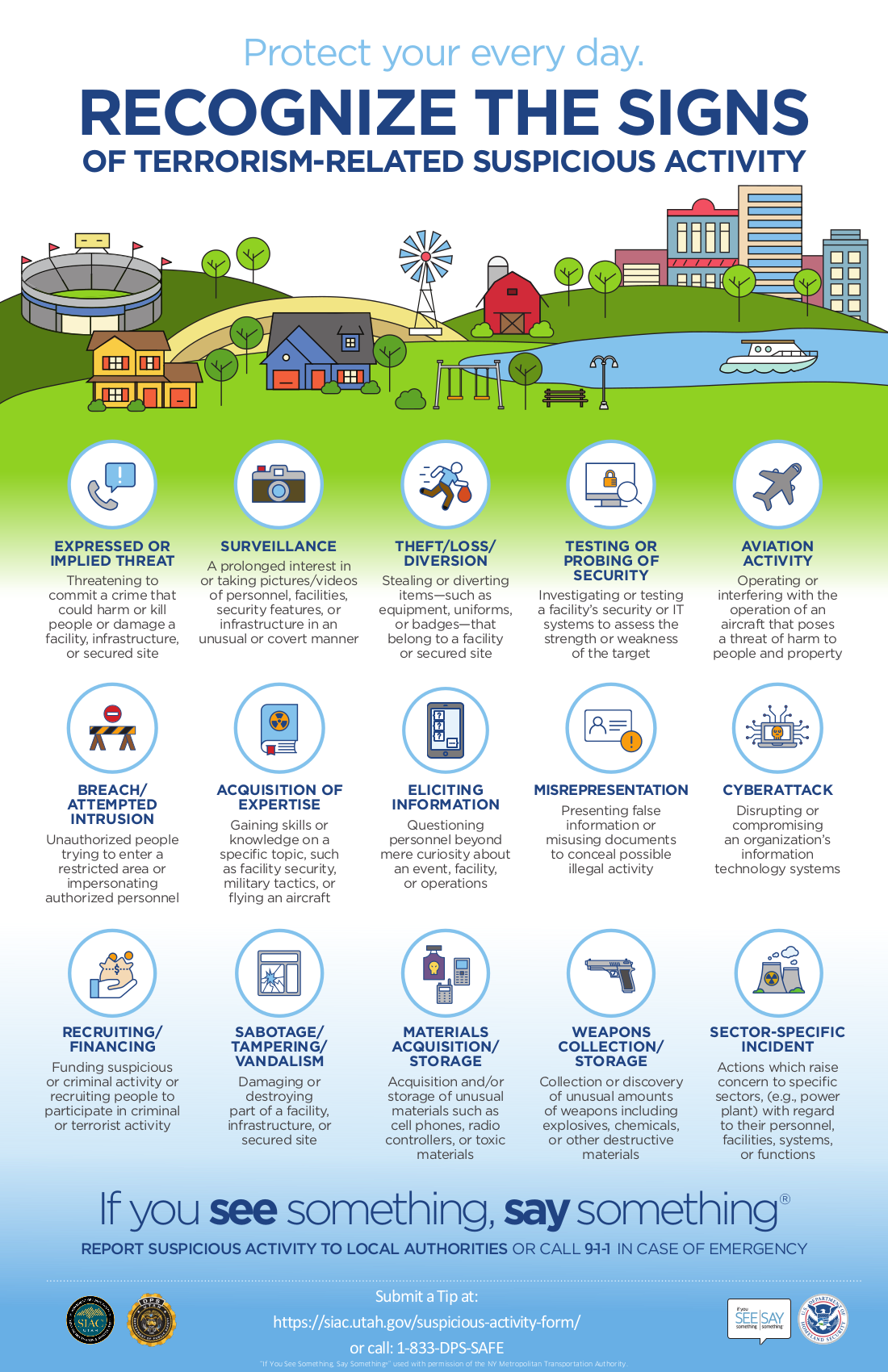
What is suspicious activity?
Mass attacks of violence violate the safety of the places we work, learn, shop, relax, and otherwise conduct our day-to-day lives. Public safety stakeholders recognize identifying individuals who pose a risk of violence is not the responsibility of law enforcement alone. As a member of your community, you are familiar with what activities are normal in your neighborhood, and what is out of place. If someone’s behavior seems odd to your normal everyday interactions with others something might not be right.
Report suspicious activity to your local law enforcement or send a tip here.
Factors such as a person’s race, ethnicity, and/or religious affiliation do not constitute suspicious activity.
What can lead a person to commit an act of targeted violence?
Warning Signs and What You Can Do
Persons typically do not just “snap” but display indicators of potentially violent behavior over time. If these behaviors are recognized, they can often be managed and treated.
This list, developed by the U.S. Department of Homeland Security, contains behaviors that a person may exhibit that could indicate a need for help. (Note: this list is not comprehensive, nor is it intended as a mechanism for diagnosing violent tendencies; please consult a licensed professional and law enforcement for further assistance).
- Unexplained increase in absenteeism; vague physical complaints
- Noticeable decrease in attention to appearance and hygiene
- Depression/withdrawal
- Resistance and overreaction to changes in policy and procedures or upon explanation of policy and procedures
- Repeated violations of site/company policies
- Increased, severe mood swings
- Noticeably unstable, emotional responses
- Explosive outbursts of anger or rage without provocation
- Suicidal discussions
- Comments about “putting things in order” or “making things right”
- Behavior typical of paranoia, (“Everybody is against me”)
- Increasingly talks of problems at home
- Escalation of domestic problems into the workplace/public sphere; talk of severe financial problems
- Talk of previous incidents of violence
- Empathy with individuals committing violence
- Increase in unsolicited comments about weapons and violent crimes
You are the first line of defense
If you witness these behaviors in one of your co-workers, patrons, or guests and are concerned about their well-being, consider discussing the problem with them, if possible, and others in a manner that might allow them to find solutions. If there appears to be many of these signs and warnings, consider contacting law enforcement.
Report suspicious activity here.
In an emergency, always call 9-1-1 or contact local law enforcement.
Signs of Suspicious Activity